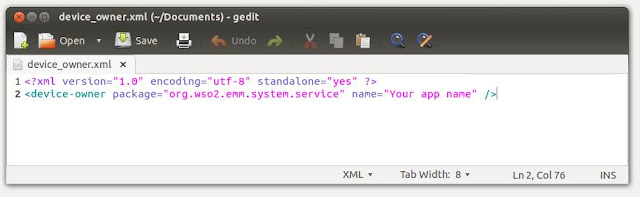
Android device auto enrollment / self enrollment in WSO2 EMM

WSO2 EMM provides capability to auto enroll a device with the server. This is done through the use of mutual SSL/TSL underneath to authenticate clients. To follow this section basics of mutual SSL is needed[1]. Let's see how the enrollment flow works. A user with adequate permission to enroll devices access the certificate section of WSO2 EMM. User generates a certificate signed by a certificate authority, upload this certificate via the certificate section in EMM console. When generating the certificate, user must make sure they provide the serial number of the device as the common name of the certificate. When uploading the certificate to EMM, it is expected to provide the same serial number as well. User also embed the generated client certificate in the Agent and compiles the Agent. Please note that for each device that needs to enroll with EMM needs to have a certificate embedded. As described in the basics of mutual SSL article[1], when the user starts the An...